X-egain-session. This header, like all HTTP headers, is case insensitive.
All ECE REST API require authenticated access. Therefore, the
first call made by a client must be to the Login API. The client then must record
X-egain-session HTTP header returned in the response and submit this
header in the subsequent calls. The header containing session ID is passed back and forth
from the client to the server during the session.
The only APIs that do not require X-egain-session header are Login API and various .../hello APIs.
If the header is not present in an incoming call for the rest of ECE REST API, the REST API
will return 401 'Unauthorized' error response.
For Knowledge APIs for Authoring:
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <Error xmlns="http://bindings.egain.com/ws/model/v12/gen/platform"> <message>User could not be authenticated. Invalid session ID.</message> </Error>
For Interaction APIs:
<?xml version="1.0" encoding="UTF-8" standalone="yes" ?> <error xmlns="http://bindings.egain.com/ws/model/v12/gen/common"> <code>401-101</code> <developerMessage>Invalid or expired 'X-egain-session' header provided. New login is required.</developerMessage> </error>
If 401 response is received from the server, the client should call Login API with valid user credentials.
Starting with ECE 15, when a user logs into ECE application consoles and is successfully authenticated, the user is automatically logged in to make calls to the interaction and authoring REST APIs. If the user logs out from ECE console, she will be automatically logged out for that session from ECE REST API.
Upon successful authentication to ECE console, a session cookie containing the user's session identifier is created and set on the user's web browser. The name of this session cookie is X-egain-session. In addition, a token to prevent Cross-Site Request Forgery (CSRF) attacks is also created by the server. The name of this token is X-egain-csrf. The same session identifier and the anti-CSRF token can be used for making calls to ECE REST APIs.
In order to make REST API calls seamlessly from ECE application console, you need to pass the session identifier (X-egain-session) as well as anti-CSRF token (X-egain-csrf) with every API request.
X-egain-session needs to be sent in as a cookie. The cookie is sent automatically by the browser if the call is made from the same browser session. X-egain-csrf needs to be sent in as a header. You need to explicitly send the X-egain-csrf header with the request. For your convenience, a utility JavaScript function getEgainSecurityToken has been provided to retrieve the value of this token. See my_activities.html file for details on how to use this function. Login as a partition administrator, and add a new custom Information pane from the Tools Console. Set the launch URL to: http://WEB_SERVER_ADDRESS/CONTEXT_ROOT/web/custom/view/my_activities.html.
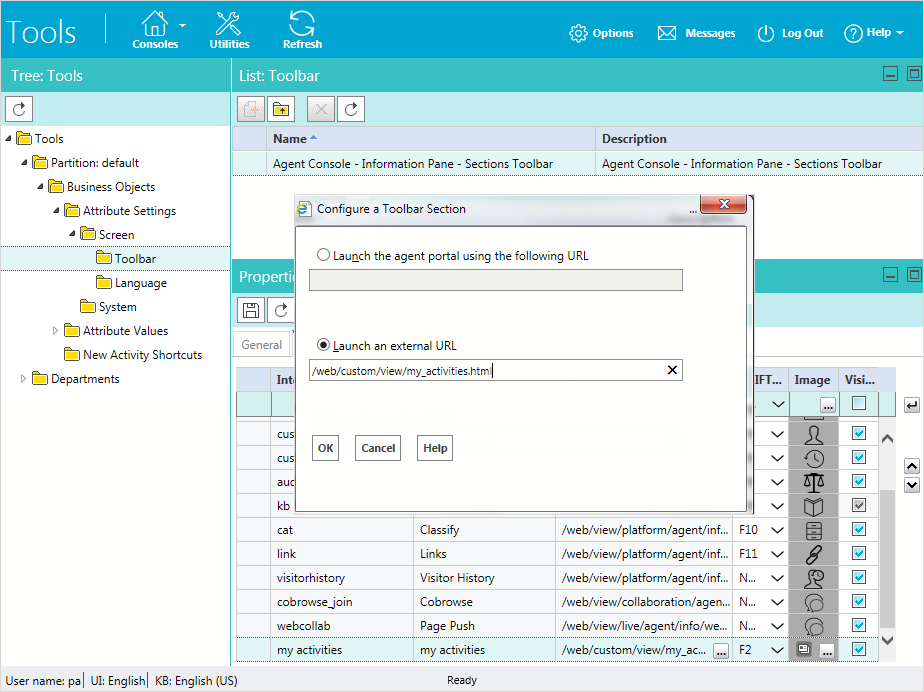
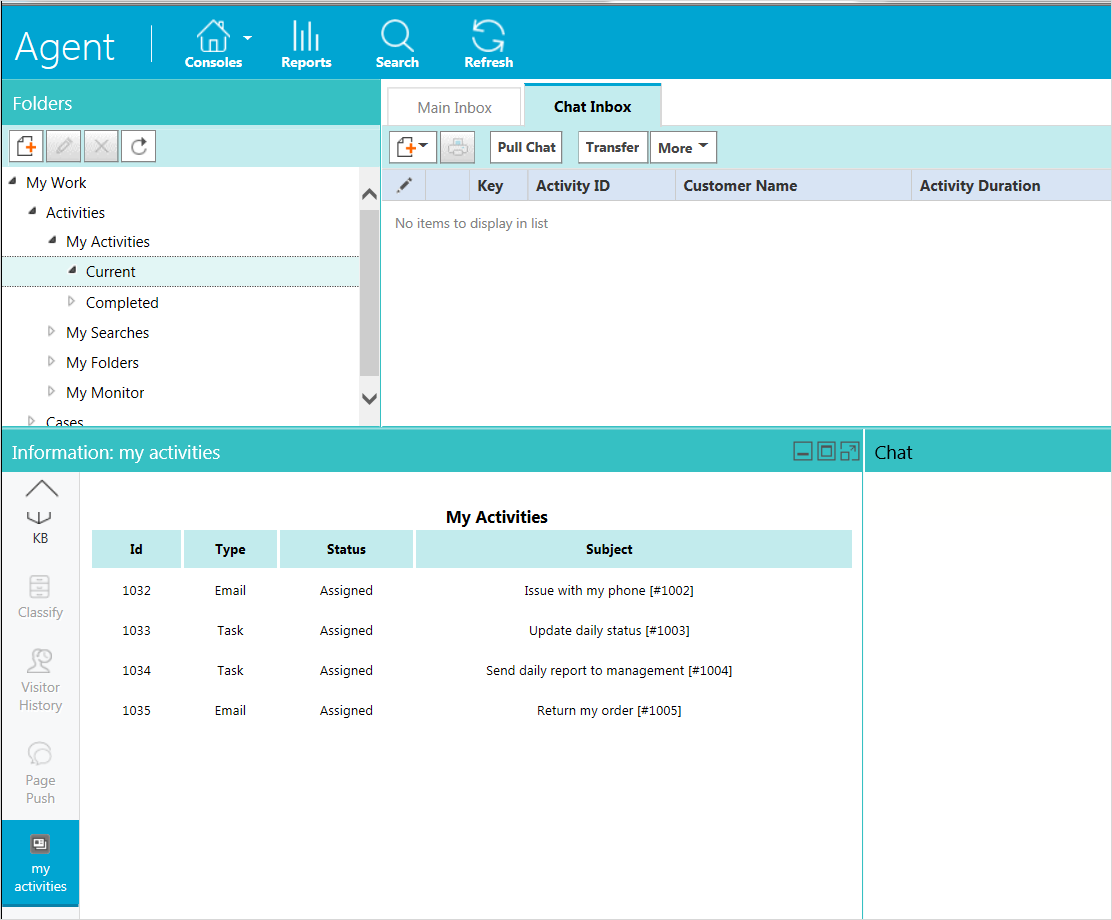
Go to the My Activities section of the Information pane. When this section loads, it will make an AJAX request to ECE REST API with X-egain-csrf request header, and browser automatically will send the X-egain-session cookie. This AJAX request makes a GET Activity API call to fetch all activities for the logged in user. Response is rendered in the Information pane.
In this example the following AJAX code snippet calls an ECE REST API using jQuery. Note that the X-egain-csrf request header sent in the request contains anti-CSRF token.
$(document).ready(function(){
$.ajax({
url:"../../../ws/v12/interaction/activity?assignedTo=" + userId,
type:'GET',
headers:{'X-egain-csrf':eGainCSRFToken,
'Accept-Language':'en-US',
'Accept':'application/json'},
complete:function(xhr, status){
if (status=='success' && xhr.status=='200')
{
// Code to render the response
}
}
}});
});