![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
nw:PathEp An abstraction of an endpoint path. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
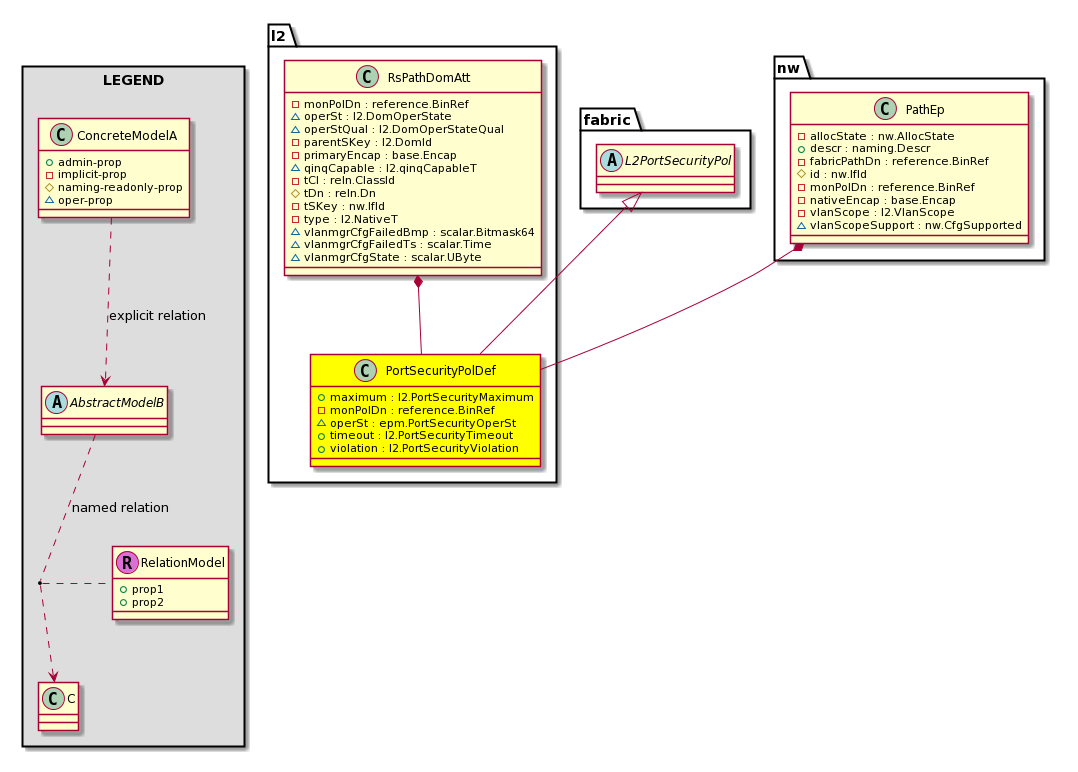
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
├
|
![[V]](styles/eye.gif) |
nw:PathEp An abstraction of an endpoint path. |
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
vlan:CktEp A VLAN object created for an endpoint group with an 802.1q encap. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:CtxSubstitute Tenant context object substitute.
Its needed for internal PE purposes but it doesnt instantiate any
VRF in the node. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Inst The infra VRF is created for the iNXOS fabric infrastructure. All communications between fabric elements, such as spine, leaf and vleaf, take place in this VRF. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
|
|
|
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
![[V]](styles/eye.gif) |
top:Root This class represents the root element in the object hierarchy.
All managed objects in the system are descendants of the Root element. |
├
|
![[V]](styles/eye.gif) |
top:System The APIC uses a policy model to combine data into a health score. Health scores can be aggregated for a variety of areas such as for the infrastructure, applications, or services. The category health score is calculated using a Lp -Norm formula. The health score penalty equals 100 minus the health score. The health score penalty represents the overall health score penalties of a set of MOs that belong to a given category and are children or direc... |
|
├
|
![[V]](styles/eye.gif) |
l3:Ctx The tenant context information is equivalent to a virtual routing and forwarding (VRF) instance created for the tenant's L3 network. Similar to a VRF in traditional Cisco routers, the tenant context isolates the IP addresses of the tenant, allowing different tenants to have overlapping IP addresses. |
|
|
├
|
![[V]](styles/eye.gif) |
l2:BD The Layer 2 Bridge-domain identifies the boundary of a tenant’s bridged/layer 2 traffic. This is similar to a VLAN in a traditional layer 2 switched network. |
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:RsPathDomAtt A source relation to the ports on this domain is allowed. This is an internal object. |
|
|
|
|
├
|
![[V]](styles/eye.gif) |
l2:PortSecurityPolDef Port Security Policy |
|