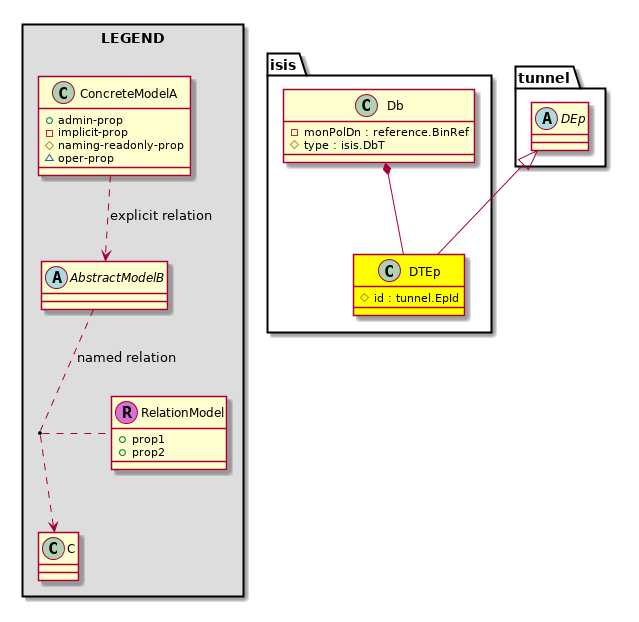
Super Mo: tunnel:DEp,
Container Mos: isis:Db (deletable:no),
|
||||||||||||
| Naming Rules | |
RN FORMAT: dtep-{[id]}
[1] PREFIX=dtep- PROPERTY = id
DN FORMAT:
[0] topology/pod-{id}/node-{id}/sys/isis/inst-{name}/dom-{name}/lvl-{type}/db-{type}/dtep-{[id]}
[1] sys/isis/inst-{name}/dom-{name}/lvl-{type}/db-{type}/dtep-{[id]}
[2] topology/pod-{id}/node-{id}/sys/isis/inst-{name}/dom-{name}/db-{type}/dtep-{[id]}
[3] sys/isis/inst-{name}/dom-{name}/db-{type}/dtep-{[id]}
|
|
| Diagram | |

Super Mo: tunnel:DEp, Container Mos: isis:Db (deletable:no), |
|
| Containers Hierarchies | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Inheritance | |||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||
| Events | |
|
|
| Faults | |
|
|
| Fsms | |
|
|
| Properties Summary | ||||||||||||
| Defined in: isis:DTEp | |
|
tunnel:EpId
address:Ip |
id (isis:DTEp:id) Overrides:tunnel:Ep:id The tunnel endpoint identifier. |
| Defined in: tunnel:Ep | |
|
tunnel:EncapT
scalar:Enum8 |
encapt (tunnel:Ep:encapt) |
|
top:NodeRole
scalar:Enum8 |
role (tunnel:Ep:role) The remote end point role type. |
|
tunnel:EpT
scalar:Bitmask32 |
type (tunnel:Ep:type) The specific type of the routed vlan interface. |
| Defined in: nw:Ep | |
|
naming:Name
string:Basic |
name (nw:Ep:name) Overrides:nw:Conn:name The name of the object. |
| Defined in: mo:Modifiable | |
|
mo:TStamp
scalar:Date |
modTs (mo:Modifiable:modTs) The time when this object was last modified. |
| Defined in: mo:TopProps | |
|
mo:ModificationChildAction
scalar:Bitmask32 |
childAction (mo:TopProps:childAction) Delete or ignore. For internal use only. |
| reference:BinRef |
dn (mo:TopProps:dn) A tag or metadata is a non-hierarchical keyword or term assigned to the fabric module. |
| reference:BinRN |
rn (mo:TopProps:rn) Identifies an object from its siblings within the context of its parent object. The distinguished name contains a sequence of relative names. |
|
mo:ModificationStatus
scalar:Bitmask32 |
status (mo:TopProps:status) The upgrade status. This property is for internal use only. |
| Properties Detail |
Type: mo:ModificationChildAction Primitive Type: scalar:Bitmask32 Units: null Encrypted: false Access: implicit Category: TopLevelChildActionComments:
| |||
Type: reference:BinRef Units: null Encrypted: false Access: implicit Category: TopLevelDnComments:
Type: tunnel:EncapT Primitive Type: scalar:Enum8 Units: null Encrypted: false Access: implicit Category: TopLevelRegularComments:
| |||
Type: tunnel:EpId Primitive Type: address:Ip Overrides:tunnel:Ep:id Units: null Encrypted: false Naming Property -- [NAMING RULES] Access: naming Category: TopLevelRegularComments:
Type: mo:TStamp Primitive Type: scalar:Date Units: null Encrypted: false Access: implicit Category: TopLevelRegularComments:
| |||
Type: naming:Name Primitive Type: string:Basic Overrides:nw:Conn:name Units: null Encrypted: false Access: admin Category: TopLevelRegularComments:
Type: reference:BinRN Units: null Encrypted: false Access: implicit Category: TopLevelRnComments:
Type: top:NodeRole Primitive Type: scalar:Enum8 Units: null Encrypted: false Access: implicit Category: TopLevelRegularComments:
| |||
Type: mo:ModificationStatus Primitive Type: scalar:Bitmask32 Units: null Encrypted: false Access: implicit Category: TopLevelStatusComments:
| |||
Type: tunnel:EpT Primitive Type: scalar:Bitmask32 Units: null Encrypted: false Access: implicit Category: TopLevelRegularComments:
| |||
|
||||||||||||